Cyber Security protects systems, networks, programs, devices, and information from cyberattacks. And in doing so it uses technologies, processes and control elements. It is often confused with information security. To explain briefly;
- Cyber security aims to protect computer systems from unauthorized access. It focuses on protecting systems from being damaged in some way.
- Information security is a broader category. It aims to protect all data sources, both digital and physical.
Computers and the internet are now an essential part of modern life. There are some areas where cyber security is of paramount importance. These are internet banking, internet shopping, e-mail and social media accounts. Important steps must be taken to prevent this information, accounts and devices from being compromised by cybercriminals.
With the increase in global cybercrime rates, Cyber Security has ceased to be a luxury or an endeavor performed only by large corporations. It is estimated that 43% of hacks in 2020 are aimed at small businesses. Therefore, an effective cyber security management should be spread from the top to the bottom of the organization. The cyber security culture supported by regular training ensures that every employee sees this as their own responsibility. Thus, in fact, security is provided by itself. In addition, quality safety and effective working practices should be continued collaboratively.

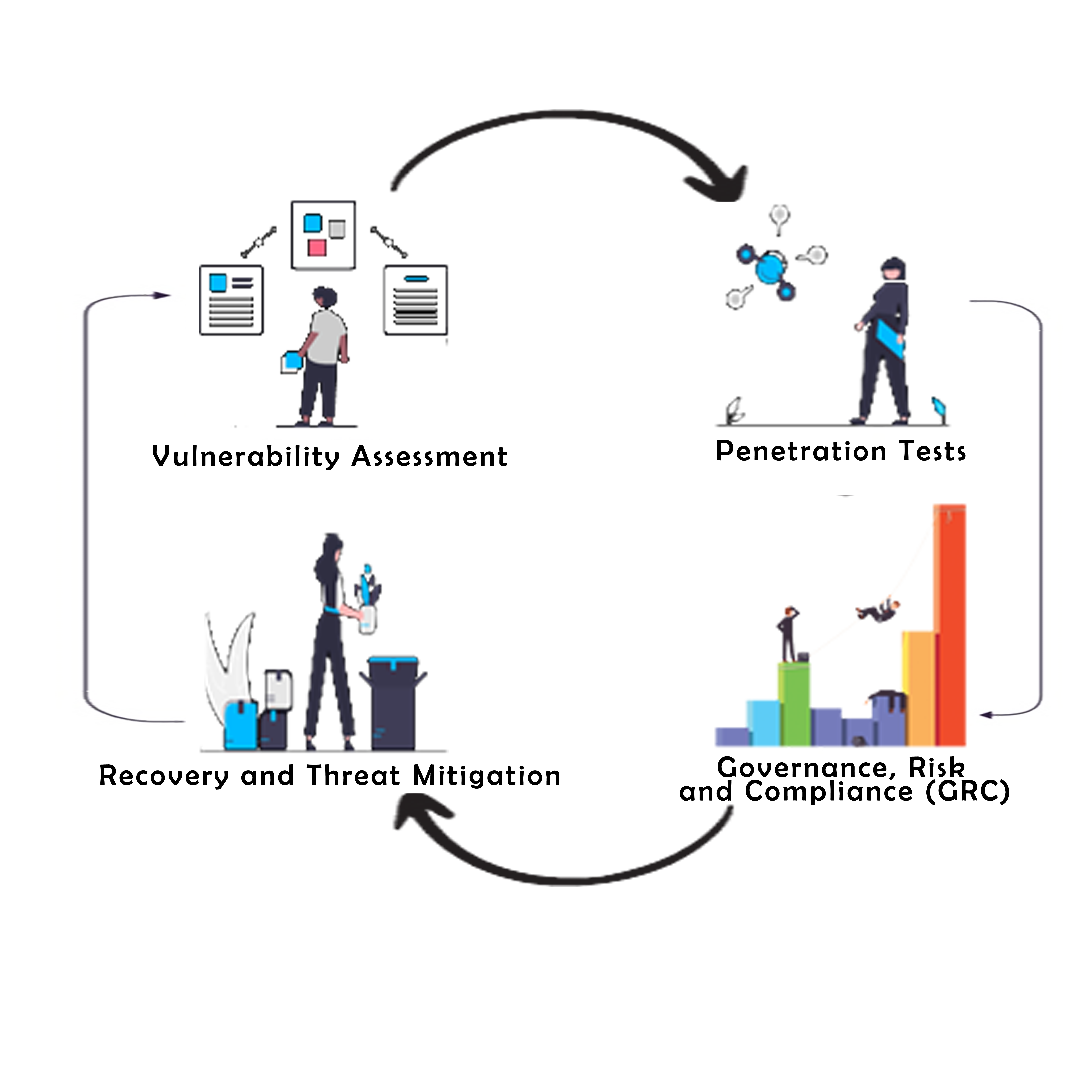
 A vulnerability assessment is the testing process used to identify and assign severity levels to as many security defects as possible in a given timeframe.
A vulnerability assessment is the testing process used to identify and assign severity levels to as many security defects as possible in a given timeframe.